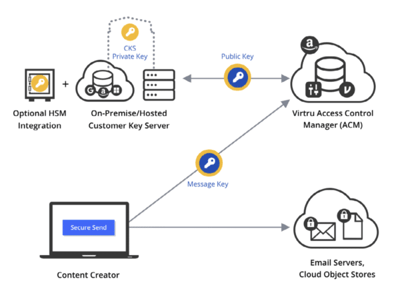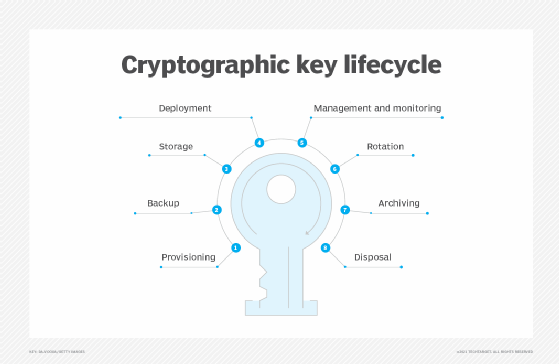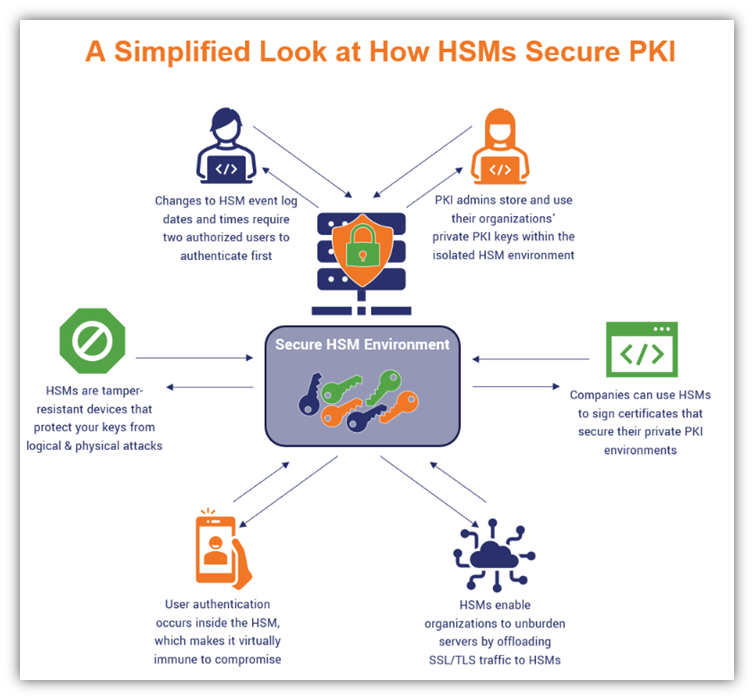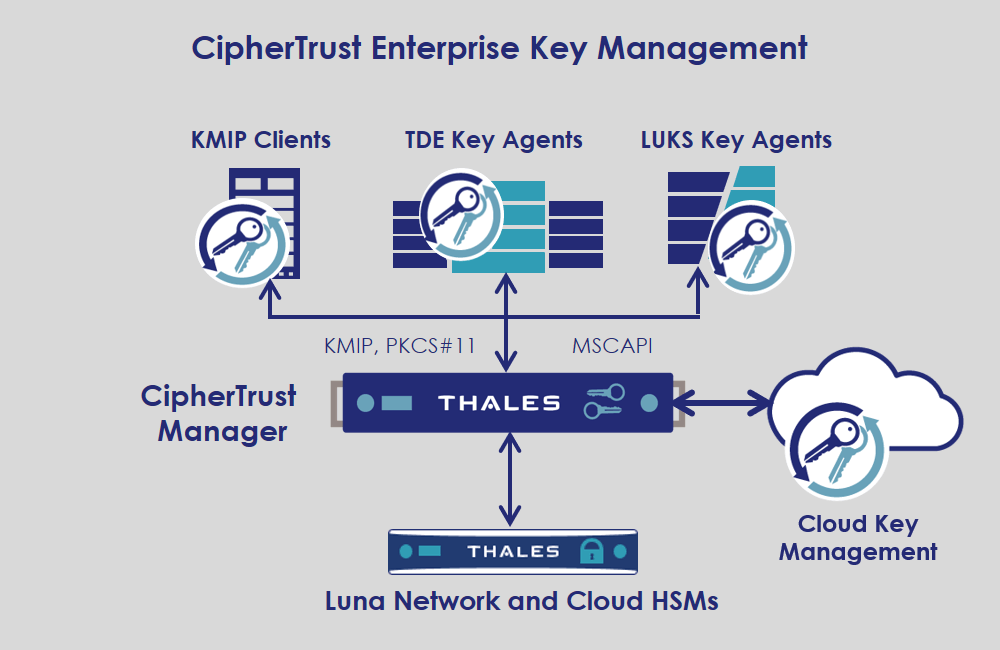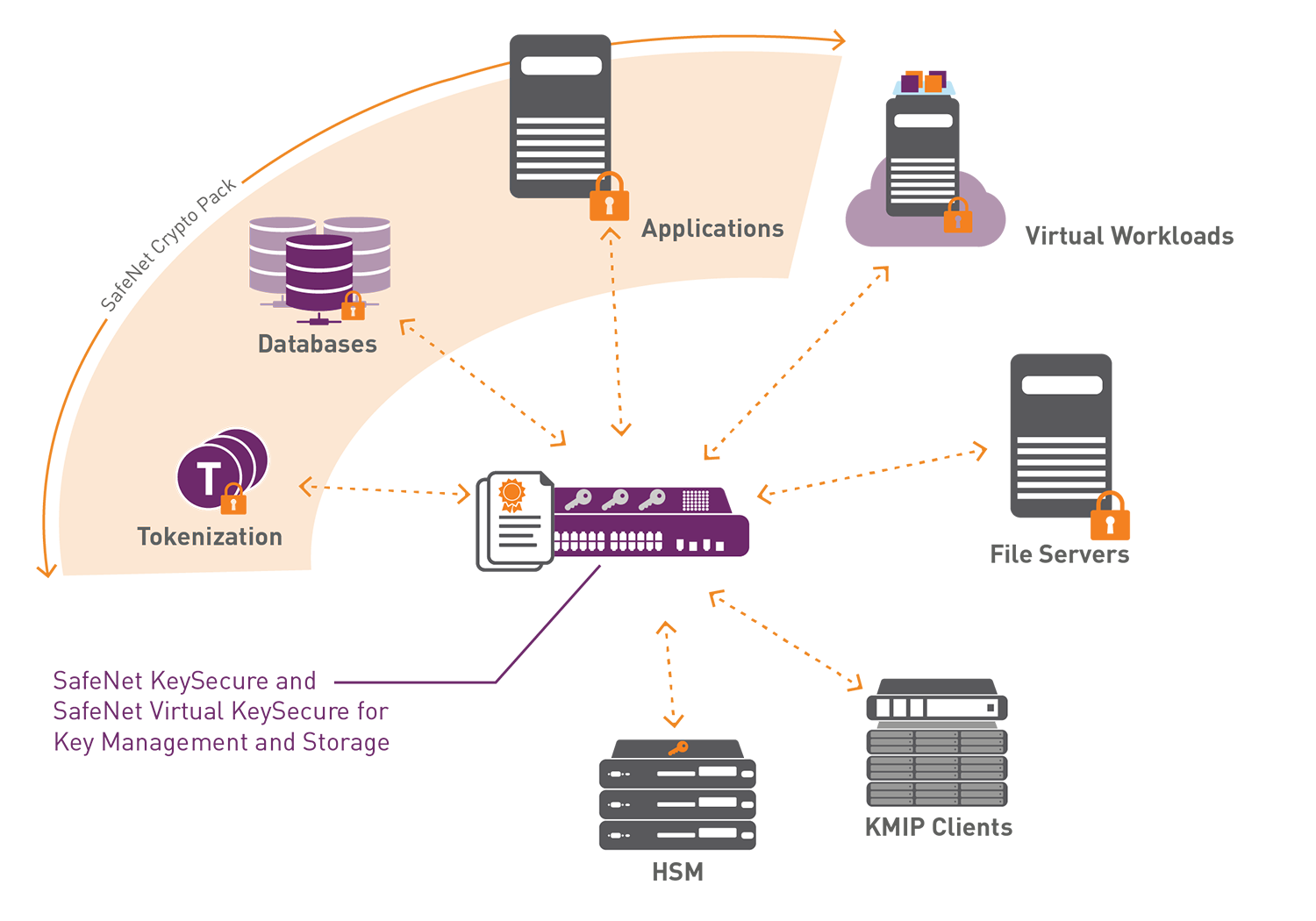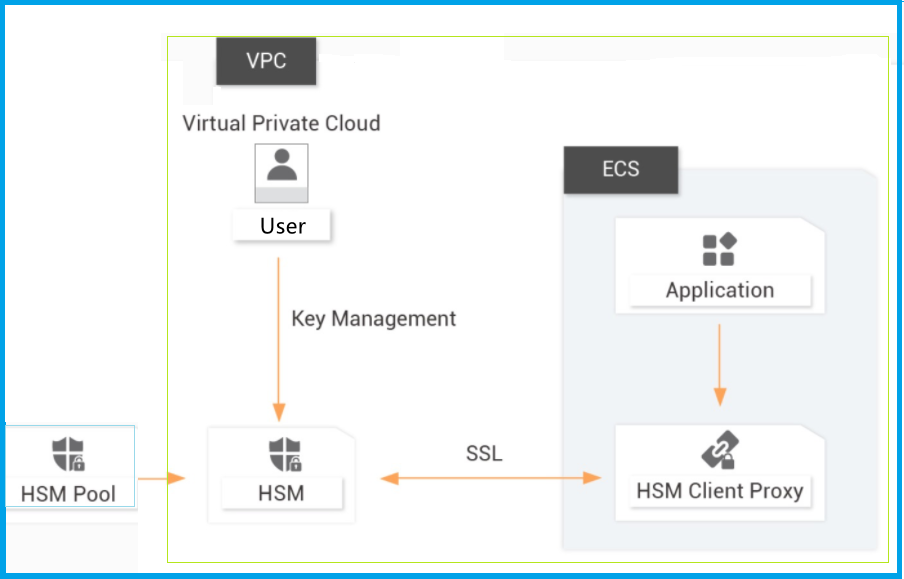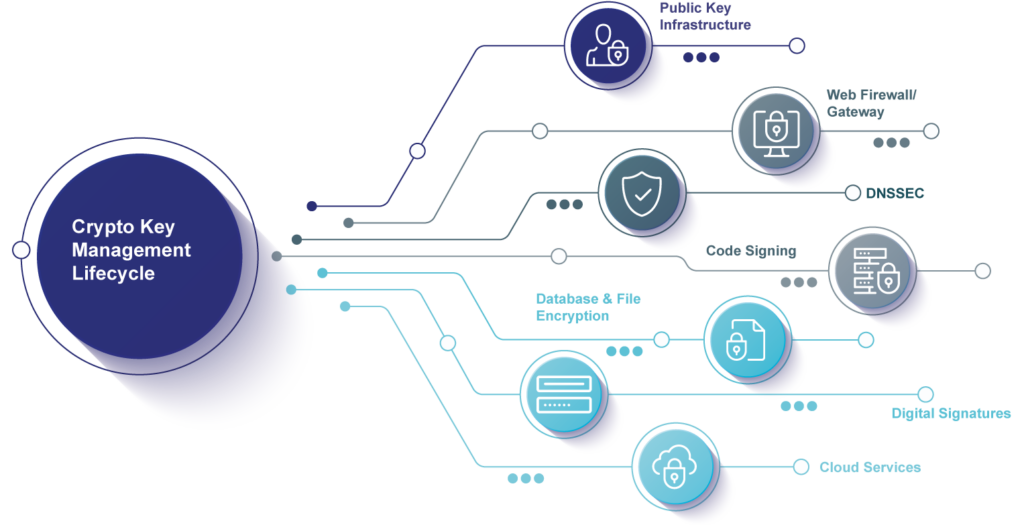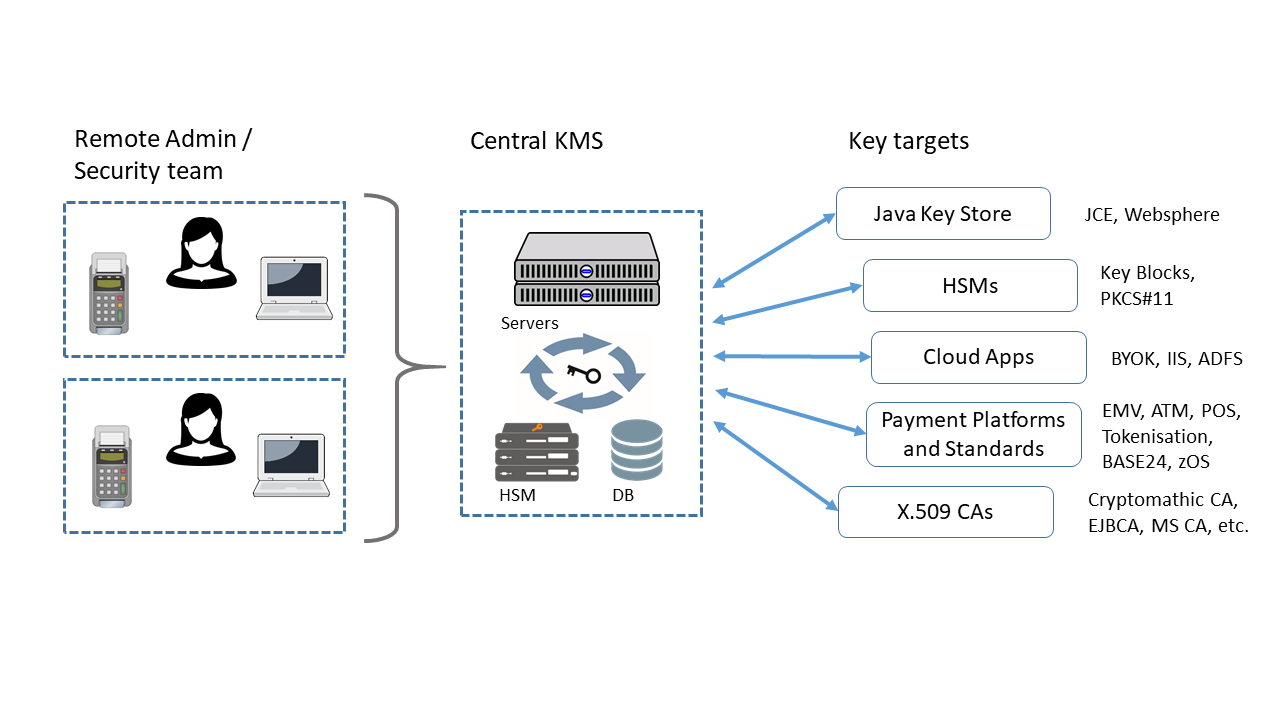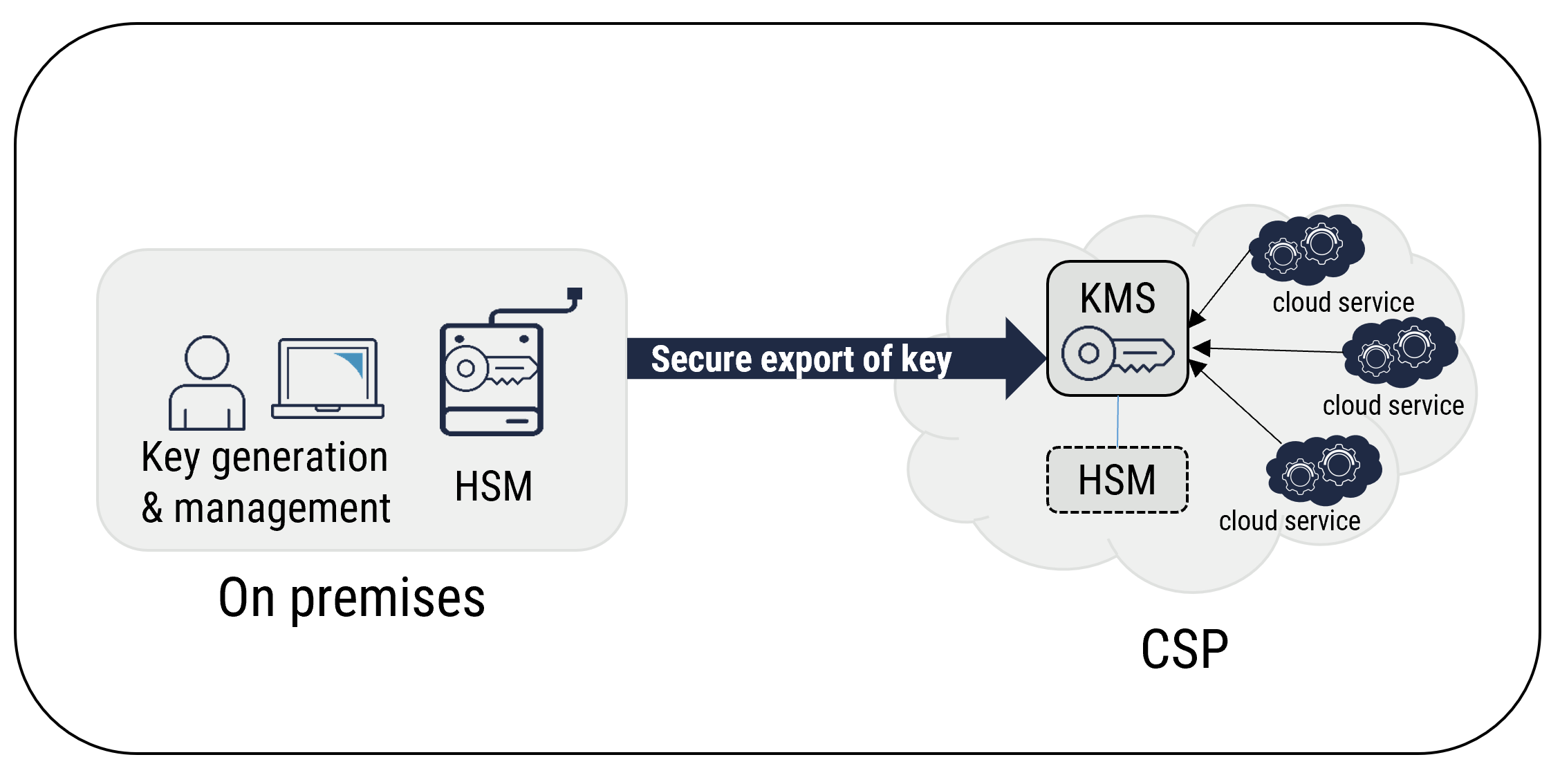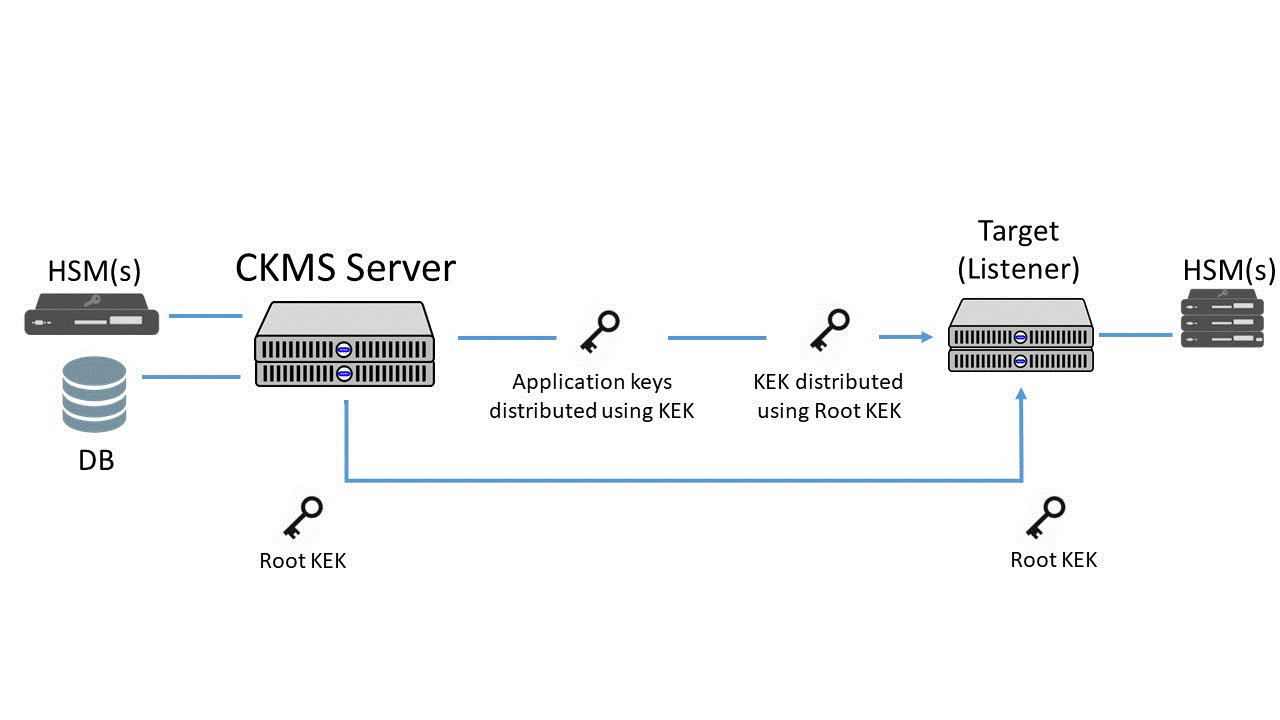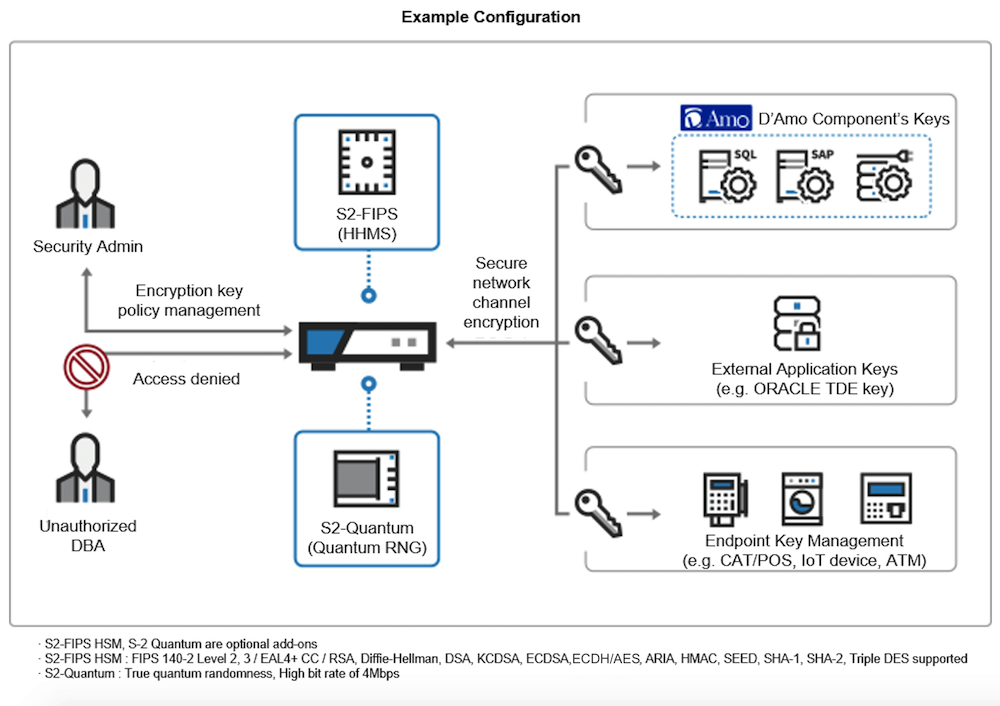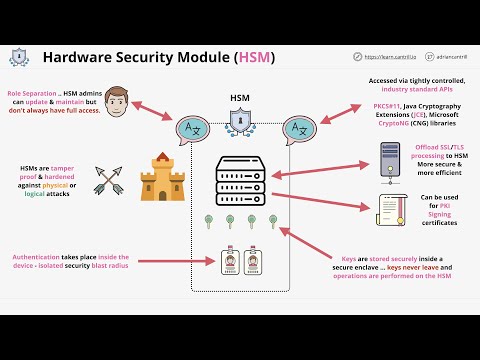
Ownership, Control, and Possession – A New AWS Feature for Key Management with the Cloud - Security Boulevard

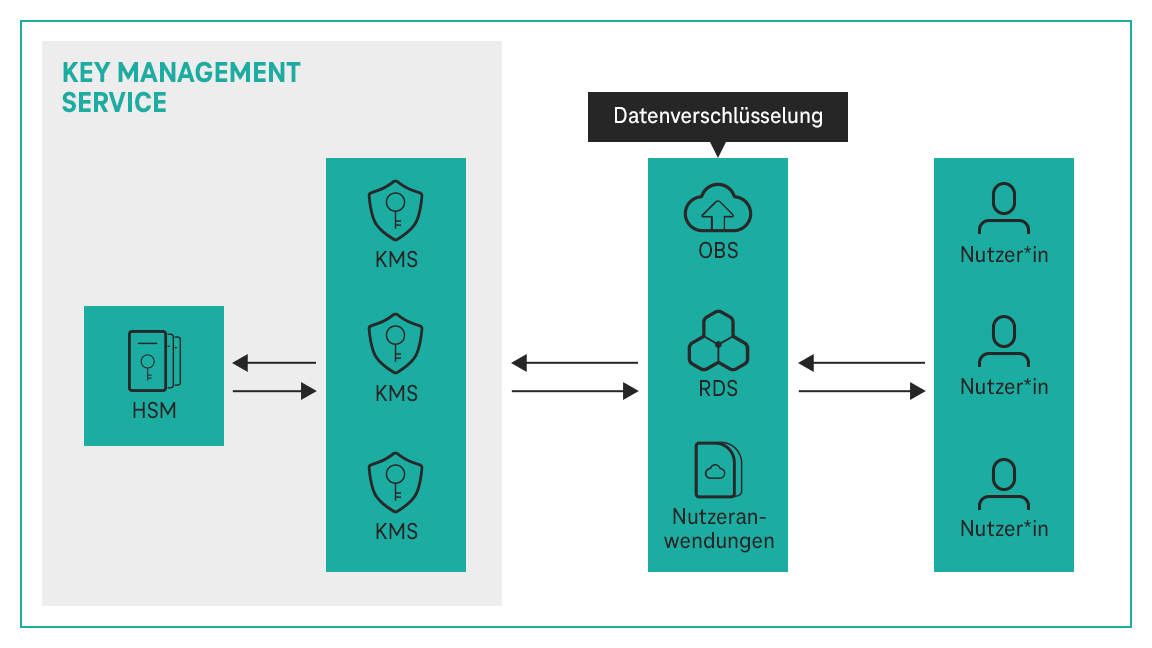
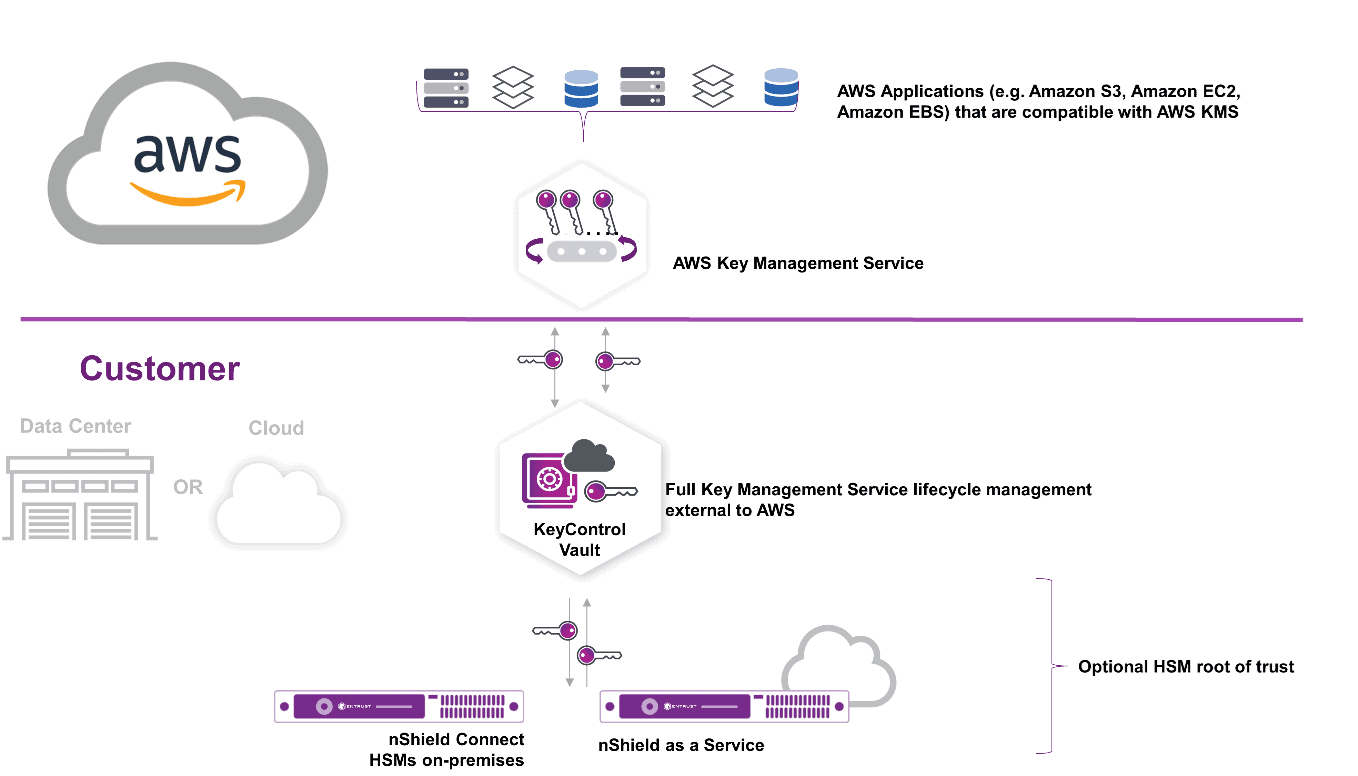
Demystifying KMS keys operations, bring your own key (BYOK), custom key store, and ciphertext portability | AWS Security Blog

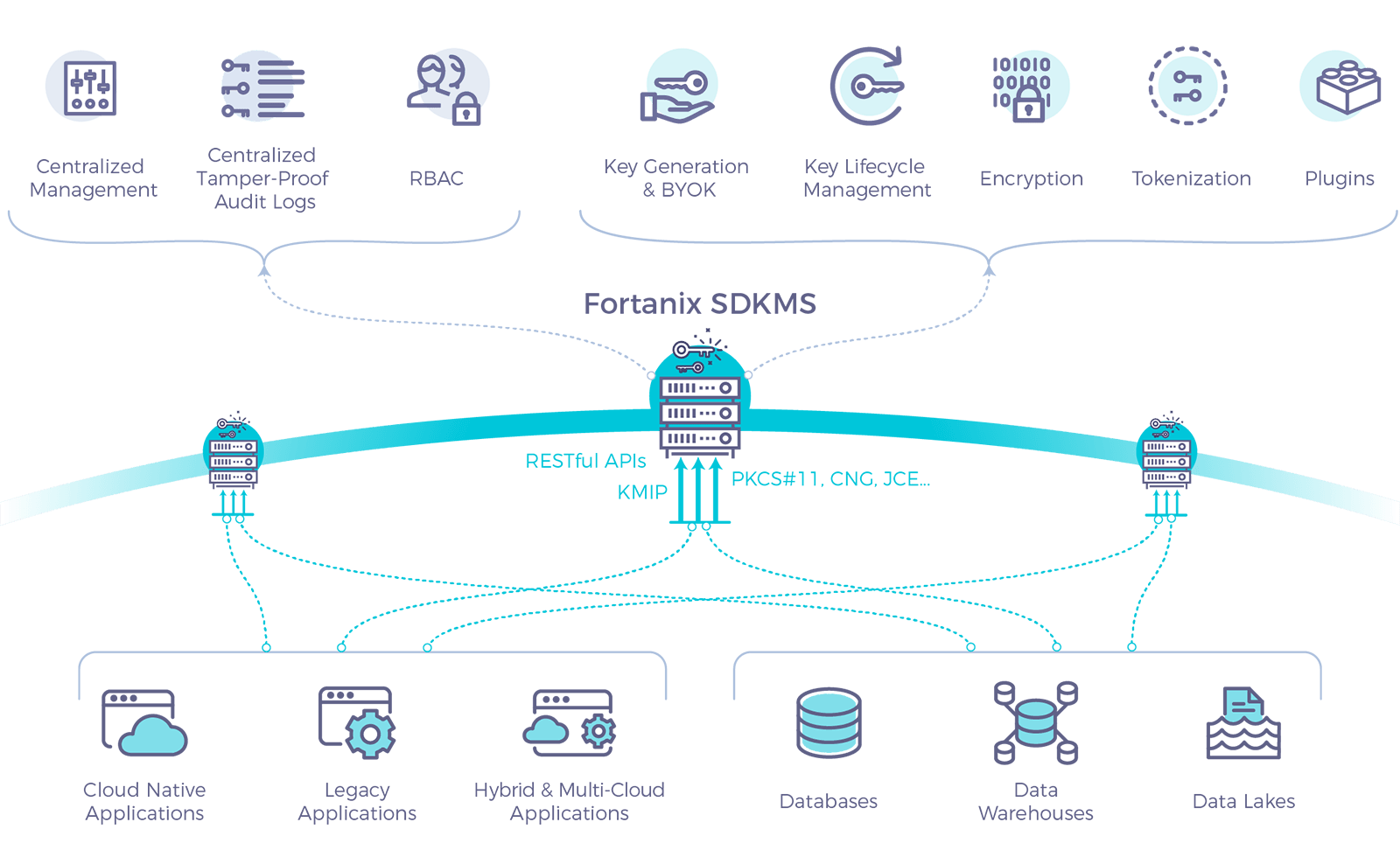
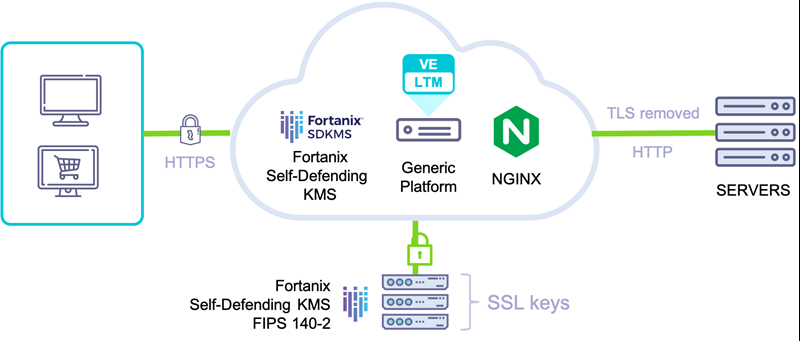
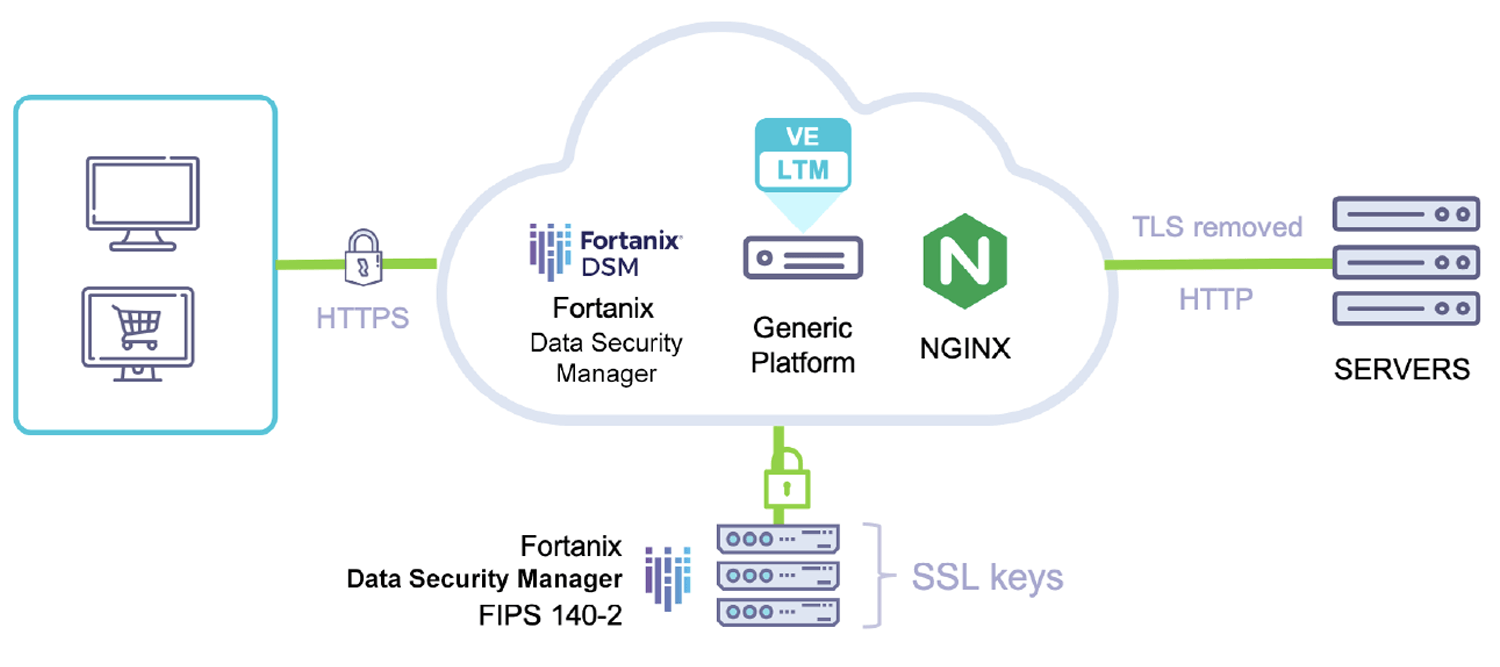
Why can't HSM and key management be provided to you as a managed service? Or can they?.. | by Fortanix | Medium