Text data size. Up: before AES-HMAC encryption and down: after AES-HMAC... | Download Scientific Diagram
Processing time to compute HMAC-SHA-256 and HMAC-SHA-384 with keys of... | Download Scientific Diagram

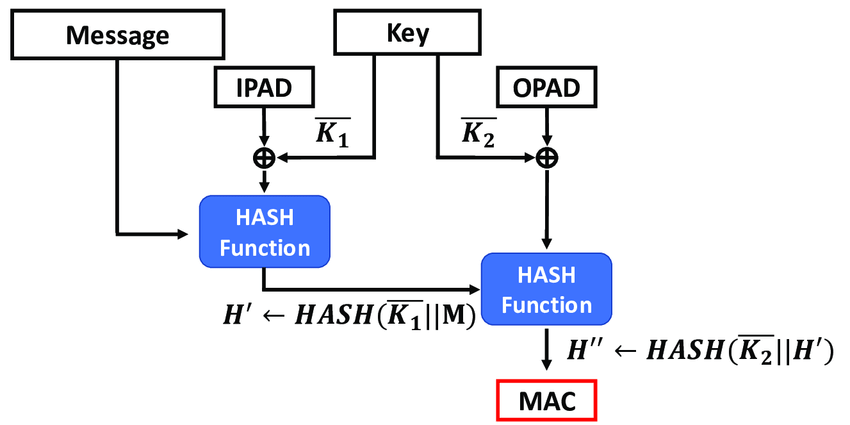
What is the HMAC message authentication system in cryptography? How to deploy it on cryptool2.1 open-source software? | by Vic | FAUN — Developer Community 🐾
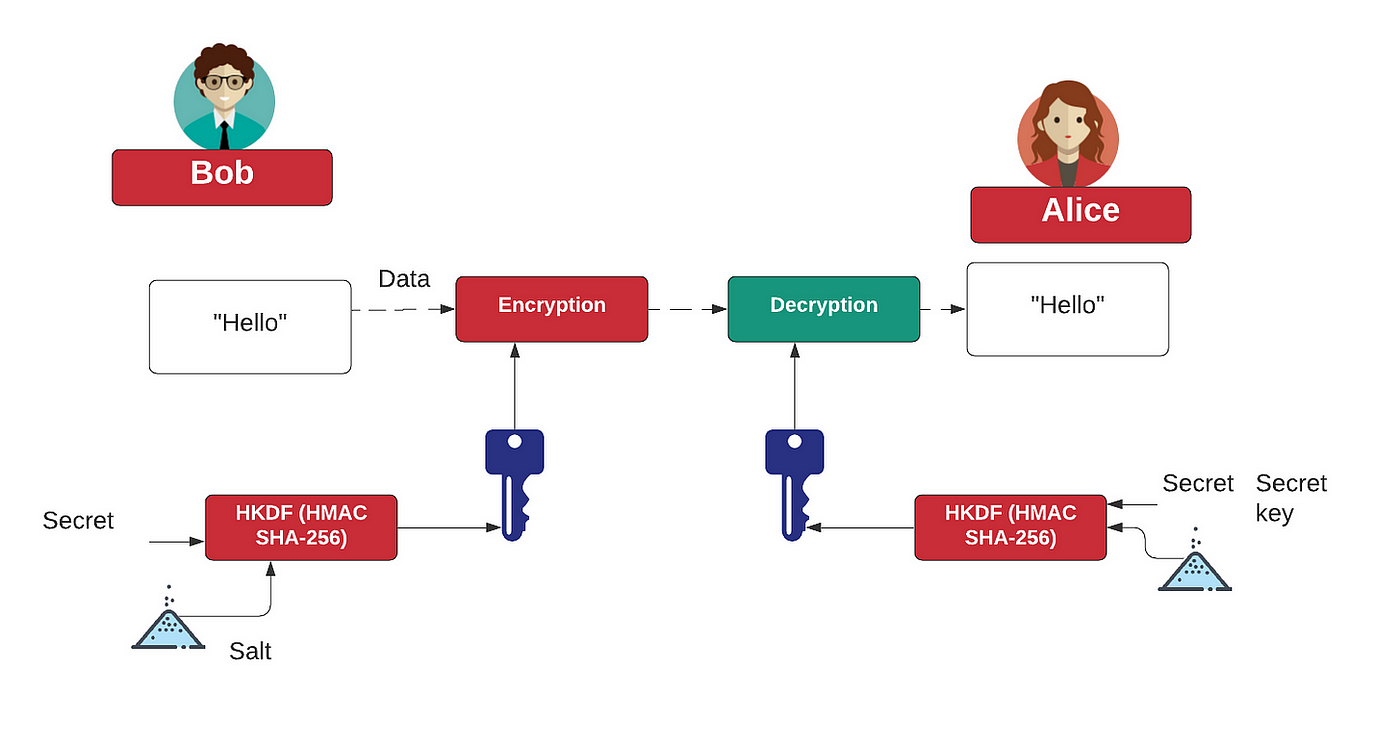
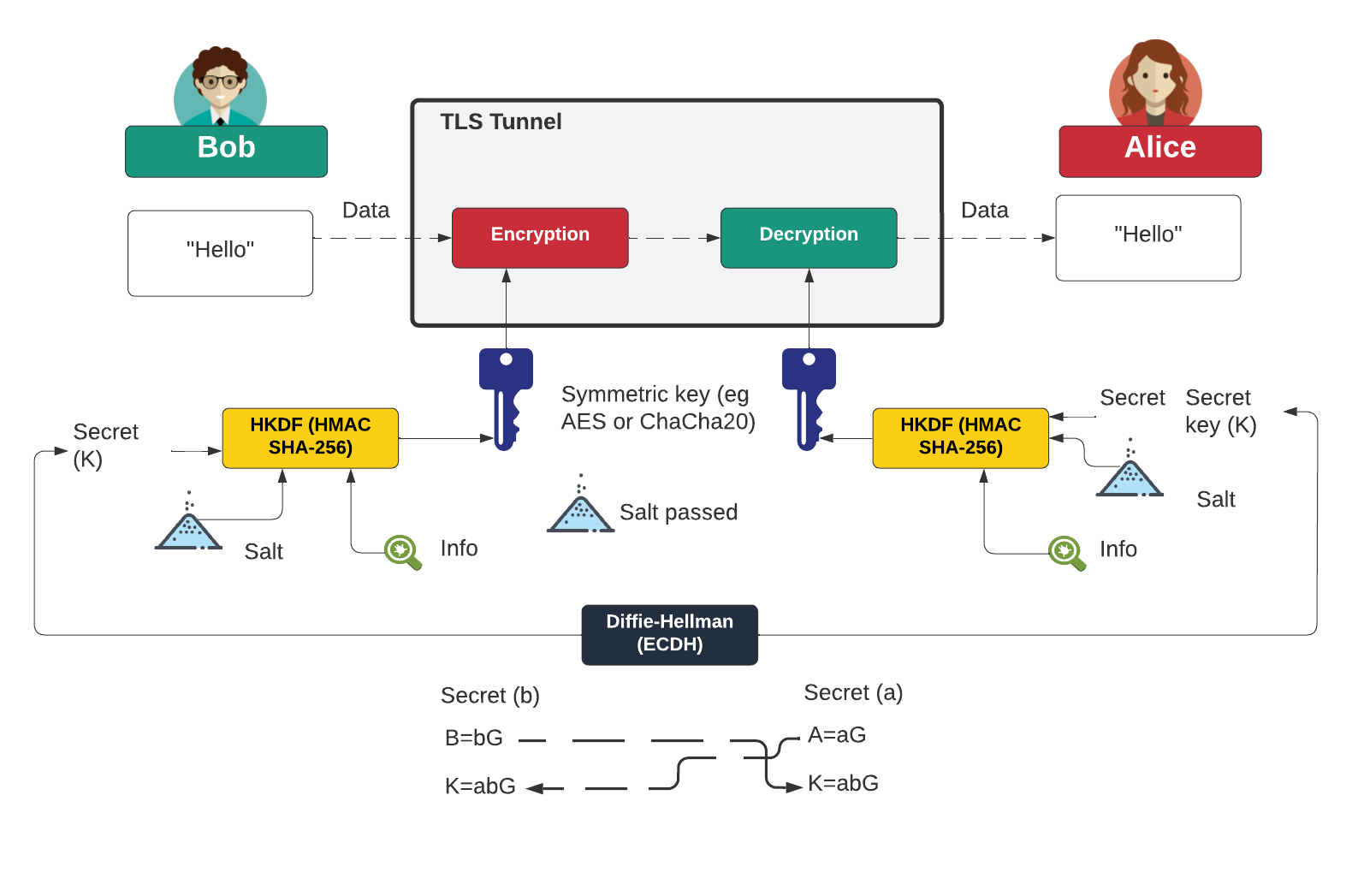
HMAC and HKDF. What's the right way to generate an… | by Prof Bill Buchanan OBE | ASecuritySite: When Bob Met Alice | Medium