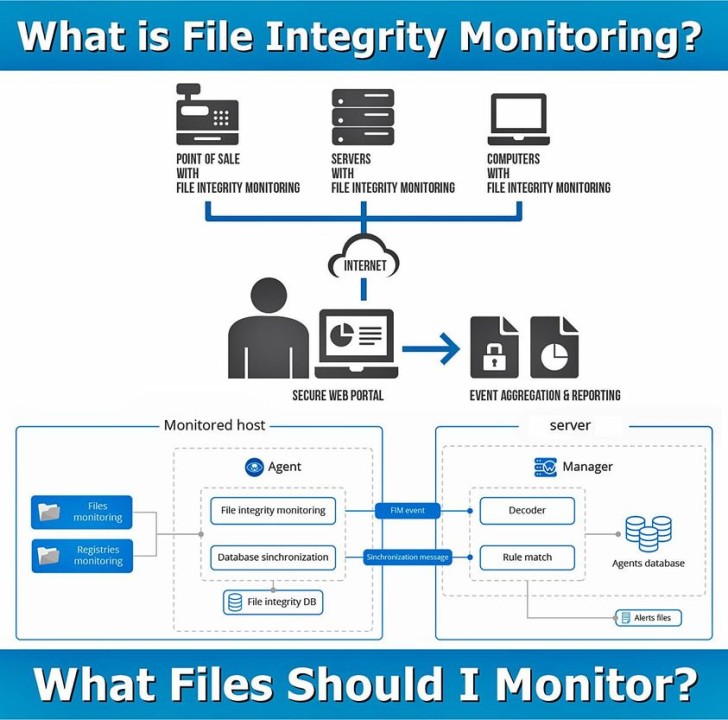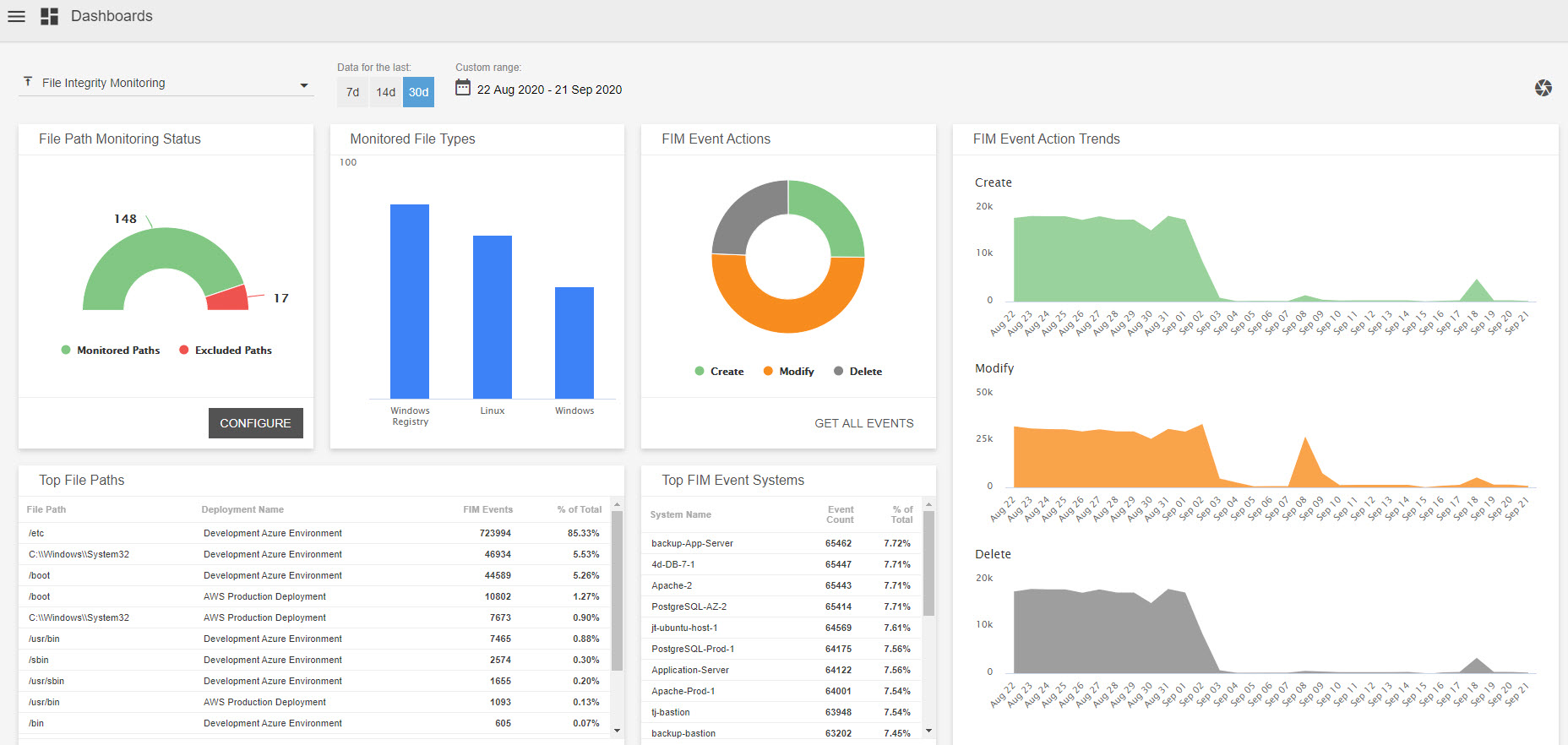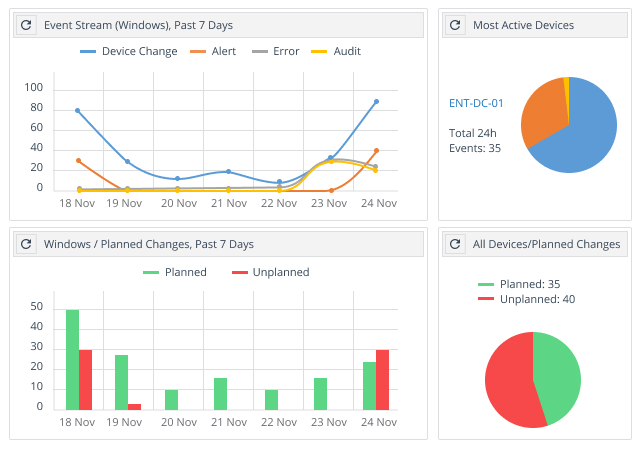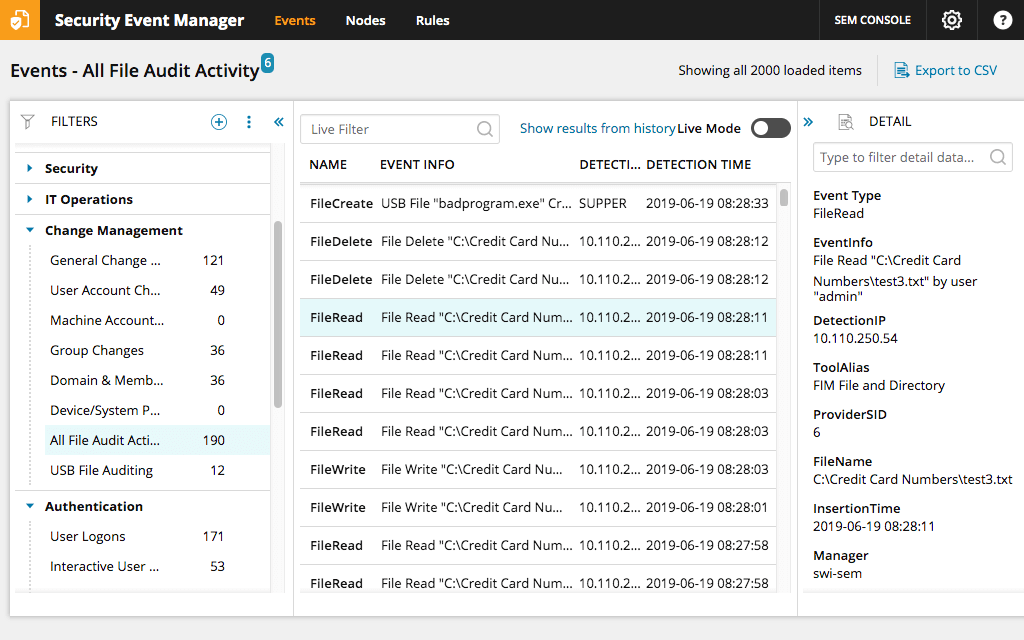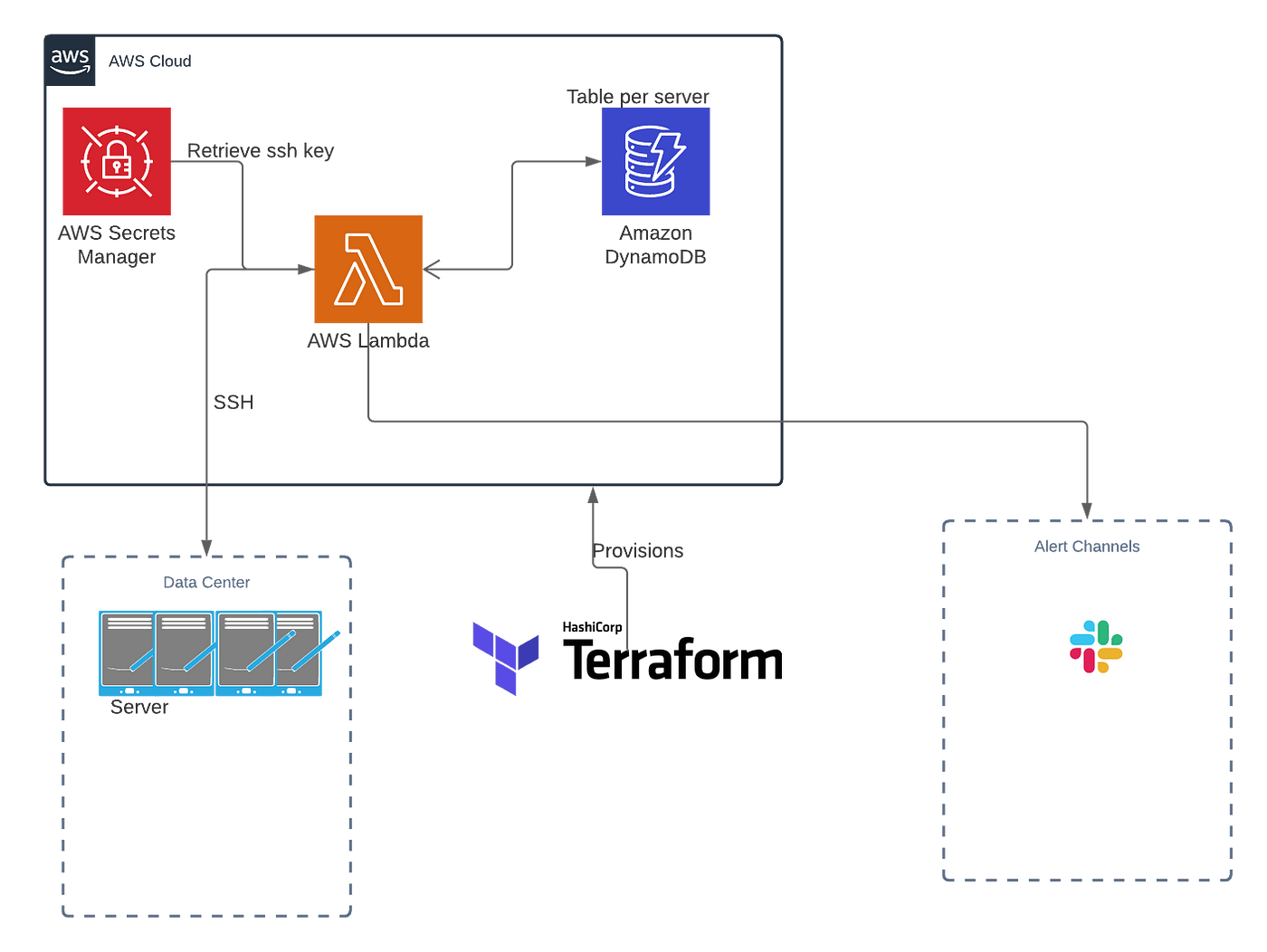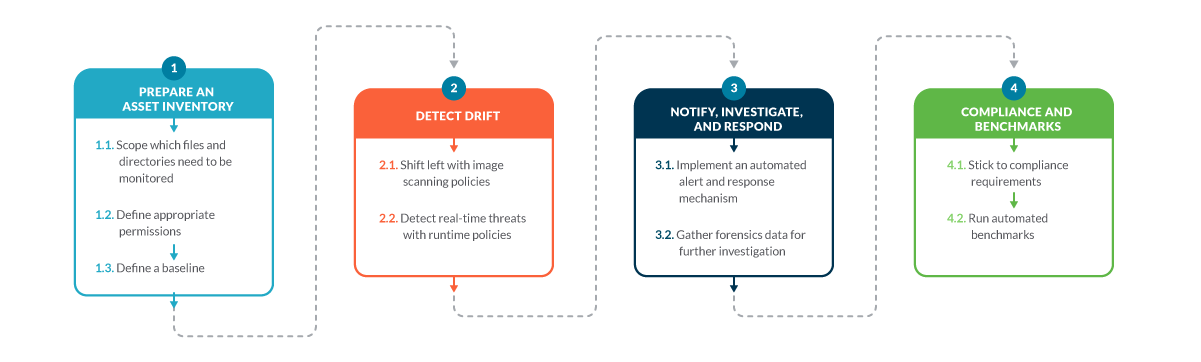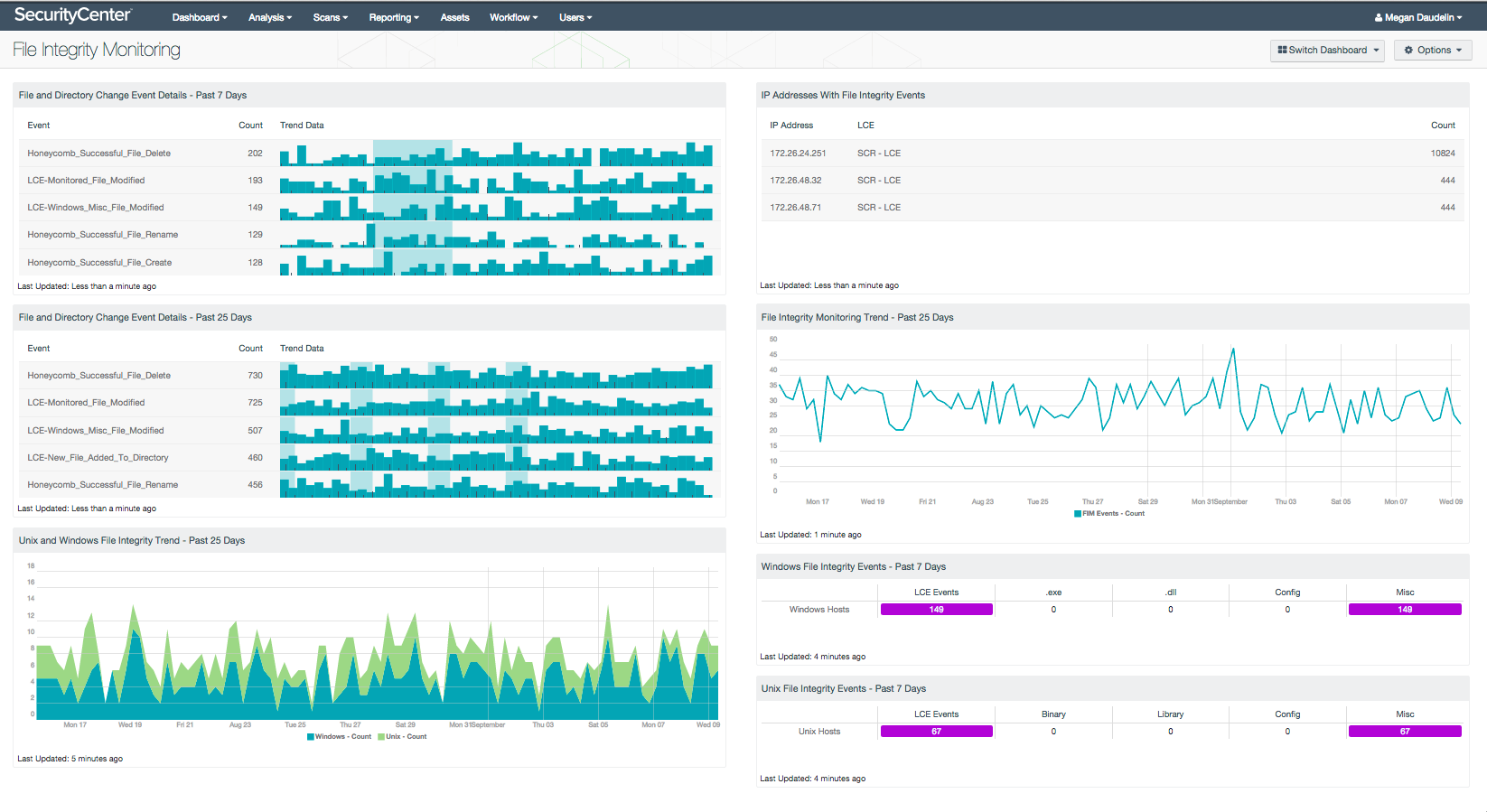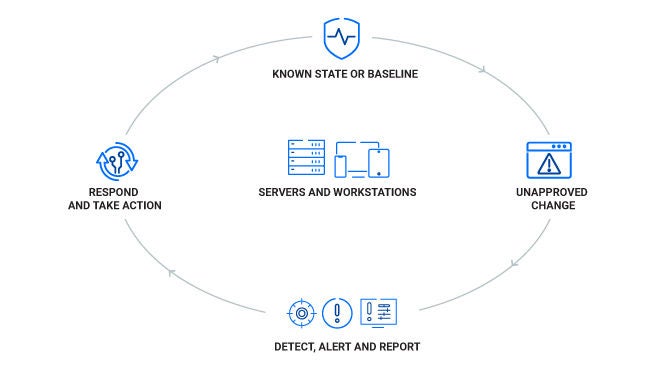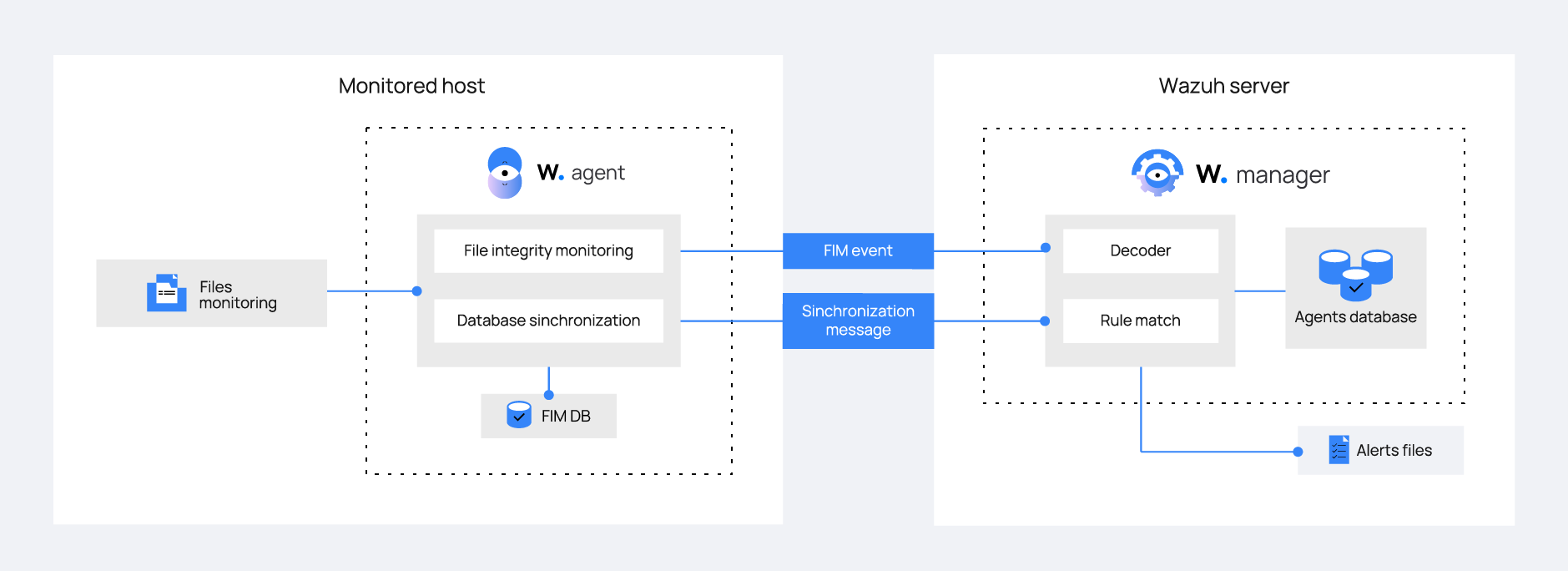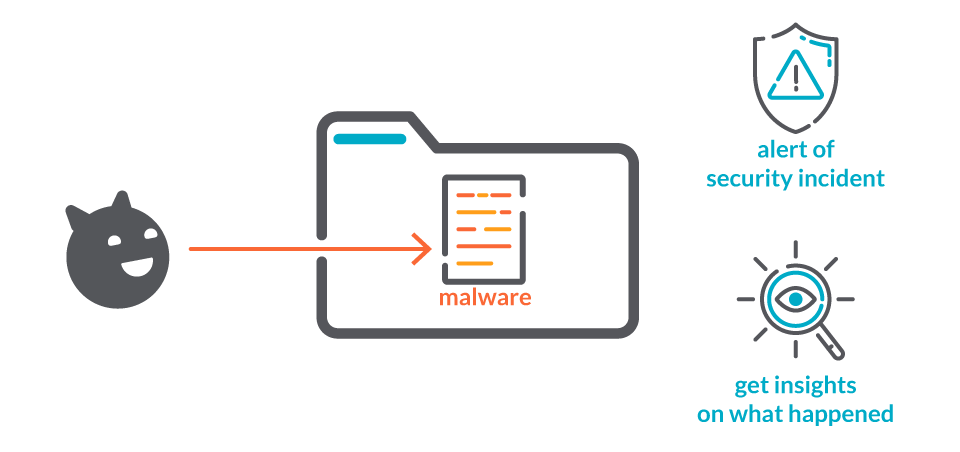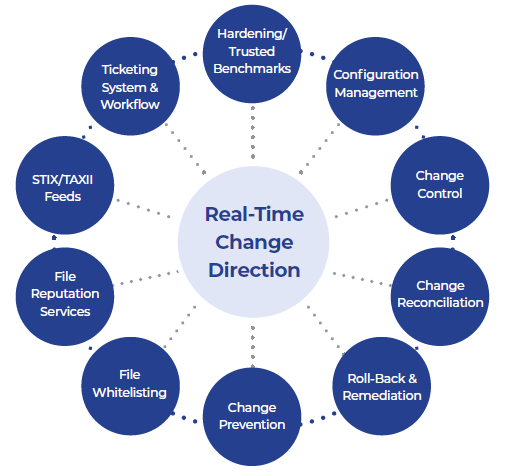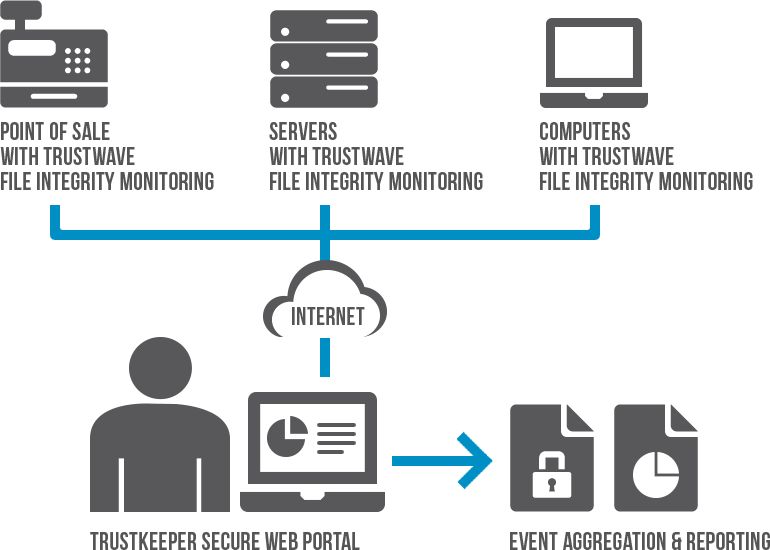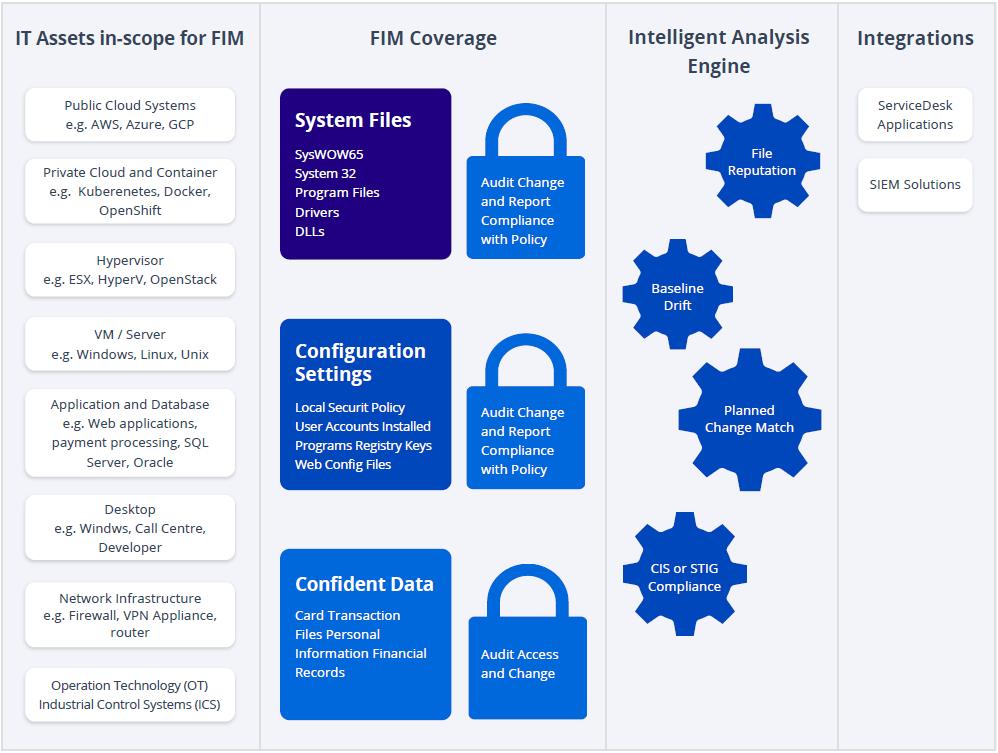
File Integrity Monitoring Tools Ppt Powerpoint Presentation Infographic Template Templates Cpb | Presentation Graphics | Presentation PowerPoint Example | Slide Templates
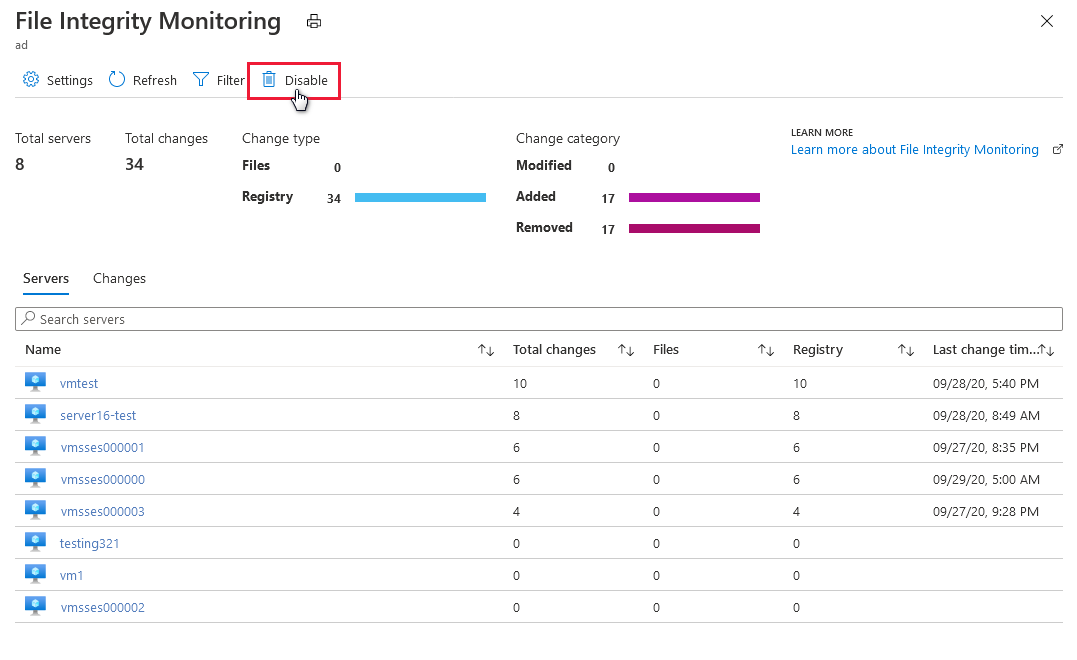
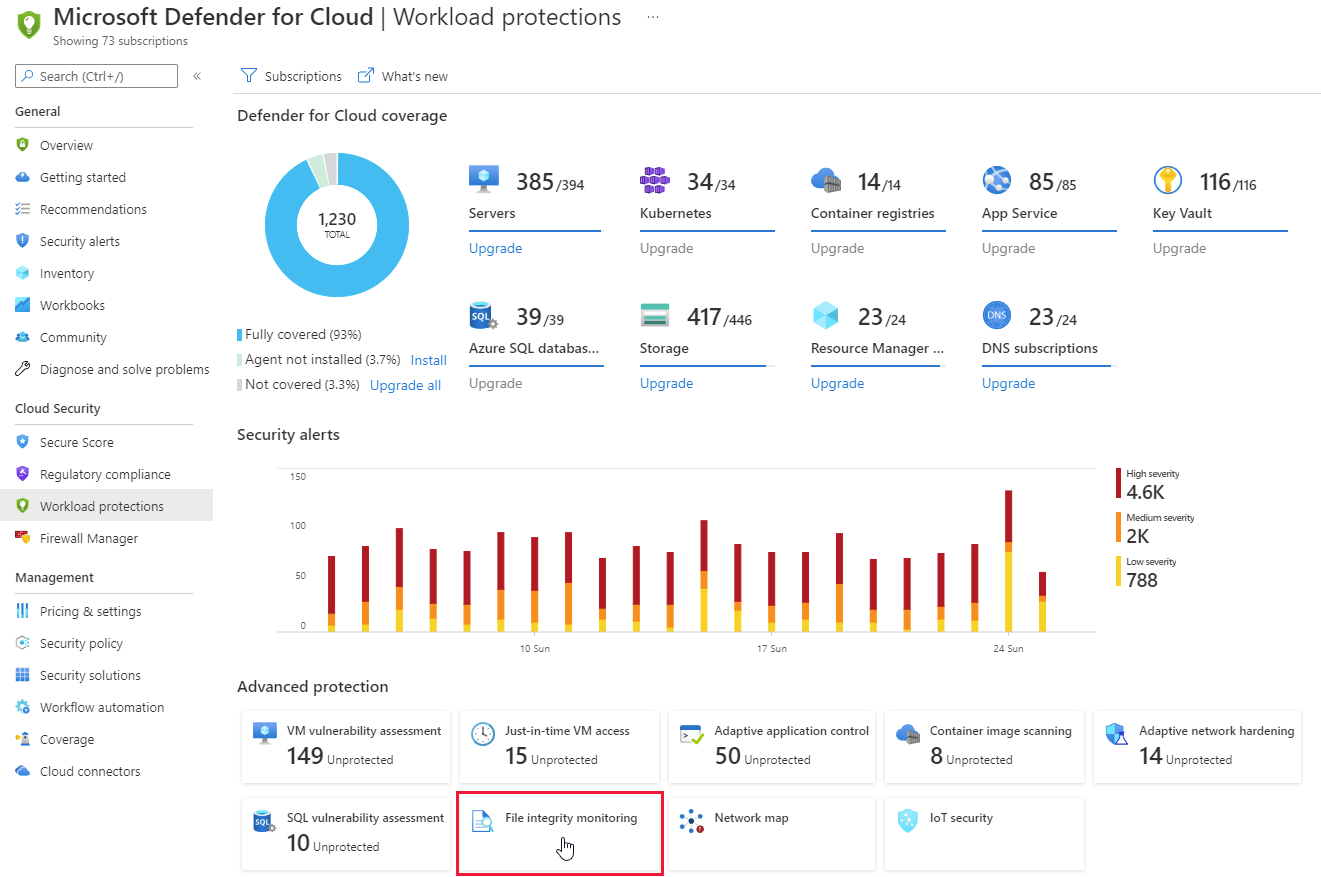
Aktivieren der Überwachung der Dateiintegrität (Log Analytics-Agent) - Microsoft Defender for Cloud | Microsoft Learn