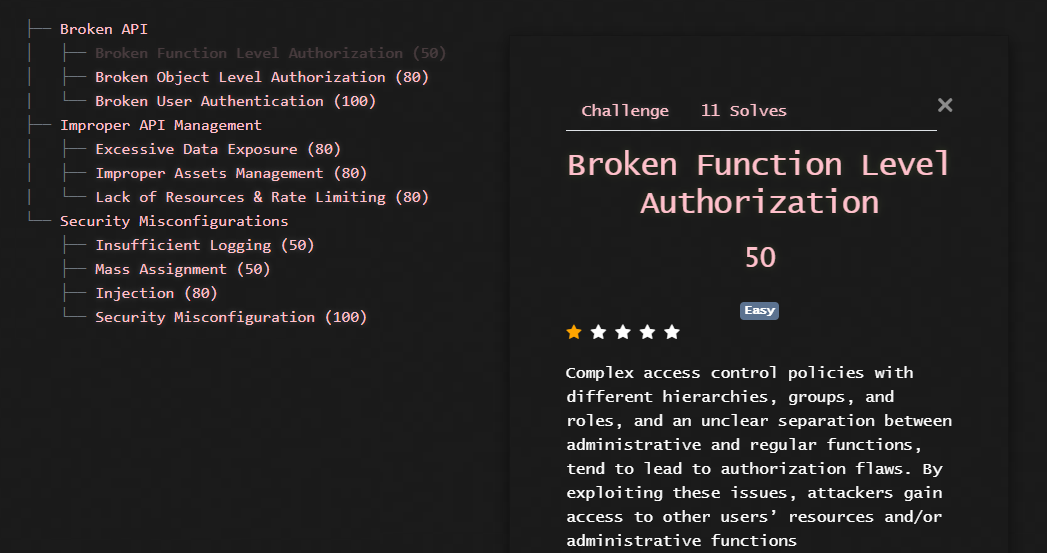
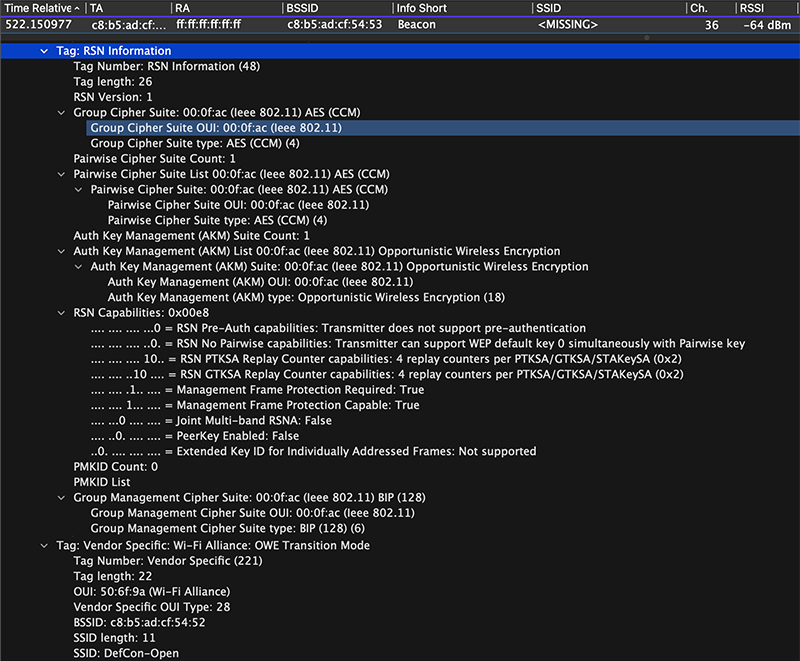
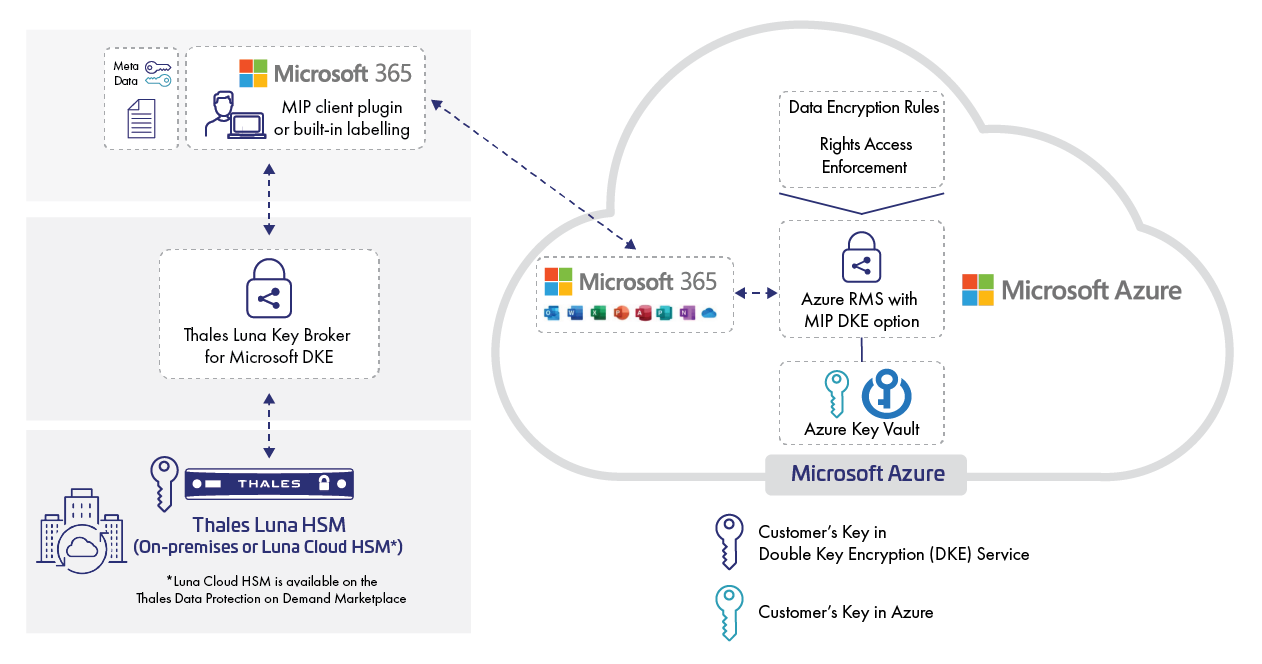
DEF CON 26 CRYPTO AND PRIVACY VILLAGE - Yueting Lee - CATs A Tale of Scalable Authentication - YouTube

Amazon.com: DefCon iProtect by DiscoverIt DD1207 Multi-Channel Signal Detector for Digital Wireless Protocols, Black : Electronics
![DEFCON 16] Bypassing pre-boot authentication passwords by instrumenting the BIOS keyboard buffer (practical low level attacks against x86 pre-boot authentication software) | PPT DEFCON 16] Bypassing pre-boot authentication passwords by instrumenting the BIOS keyboard buffer (practical low level attacks against x86 pre-boot authentication software) | PPT](https://image.slidesharecdn.com/defcon16brossard-100918053407-phpapp02/85/defcon-16-bypassing-preboot-authentication-passwords-by-instrumenting-the-bios-keyboard-buffer-practical-low-level-attacks-against-x86-preboot-authentication-software-40-320.jpg?cb=1668017545)
DEFCON 16] Bypassing pre-boot authentication passwords by instrumenting the BIOS keyboard buffer (practical low level attacks against x86 pre-boot authentication software) | PPT