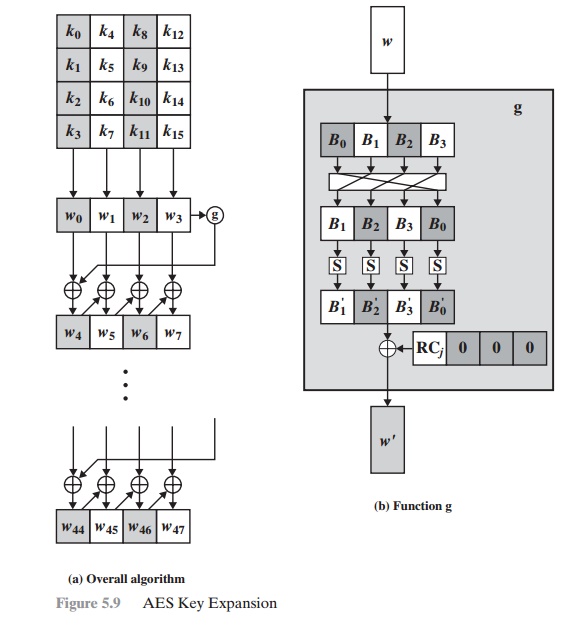
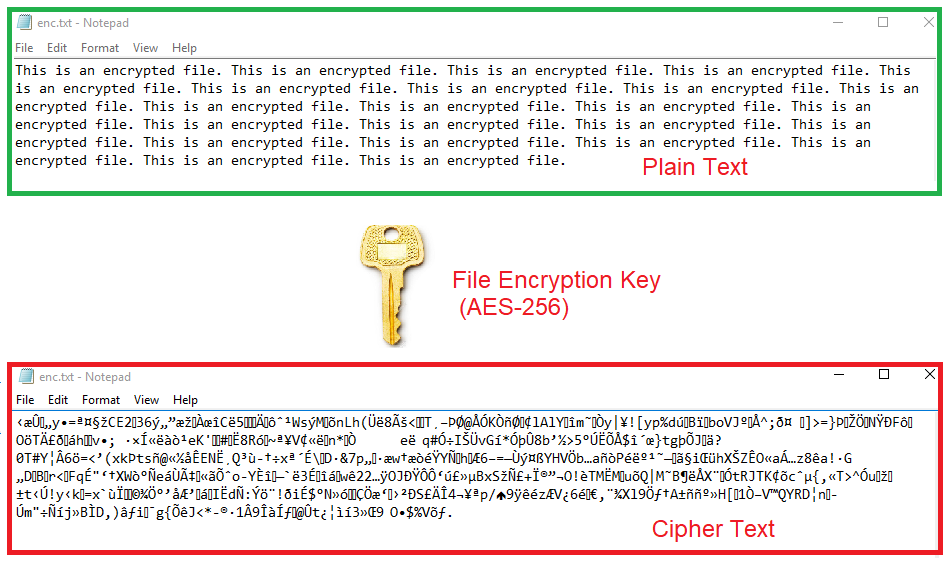
GitHub - rexdivakar/InstaEncrypt: This is an Open Source AES Standard encryption tool. It uses asymmetric-key algorithm, for both encrypting and decryption the data.

Hybrid Encryption Model Based on Advanced Encryption Standard and Elliptic Curve Pseudo Random | IntechOpen
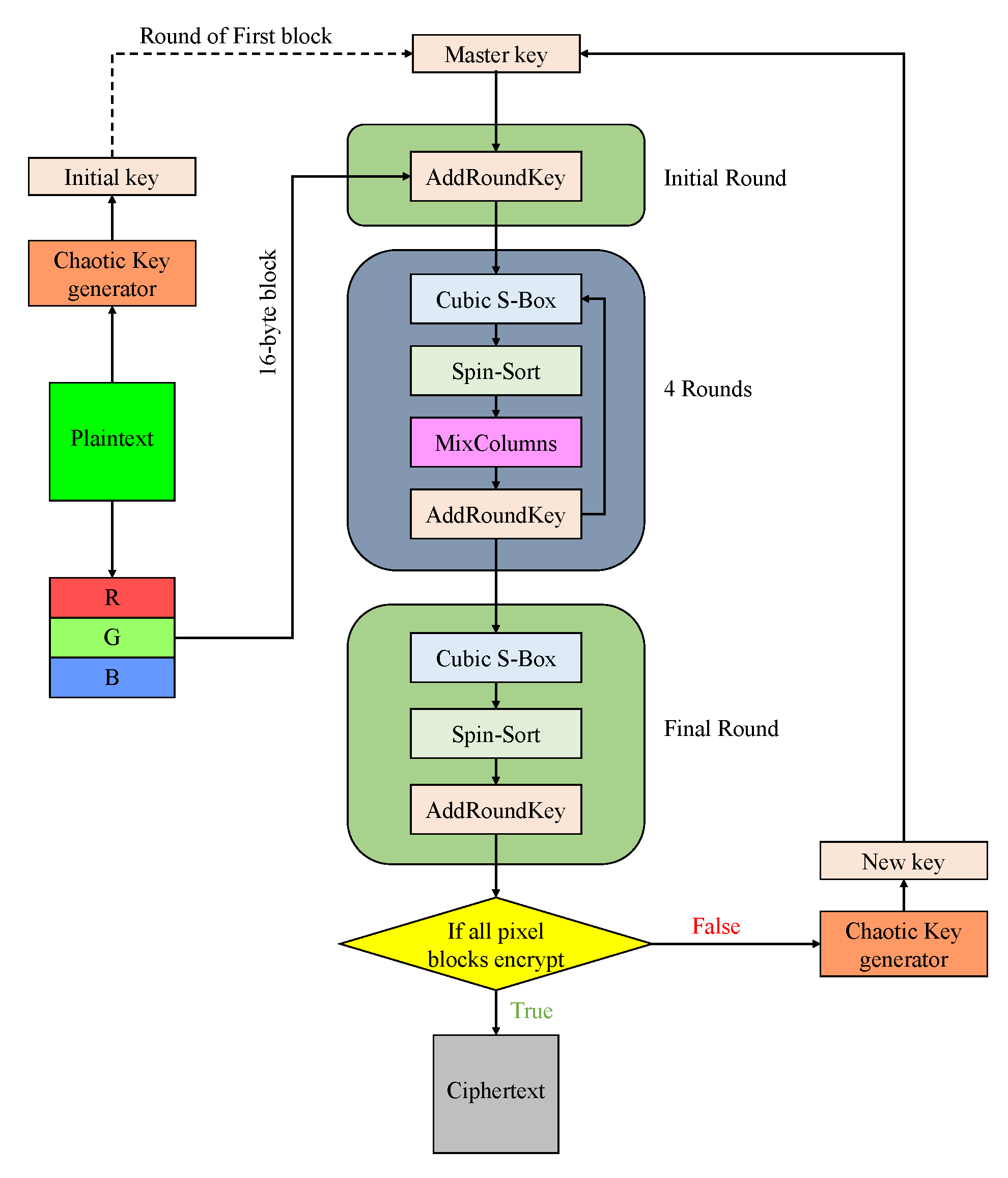
Symmetry | Free Full-Text | FPGA Implementation and Design of a Hybrid Chaos-AES Color Image Encryption Algorithm

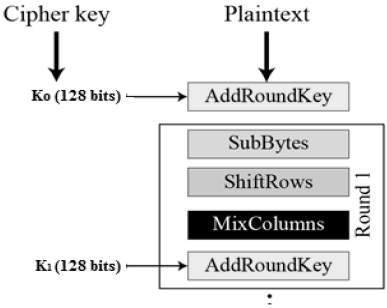
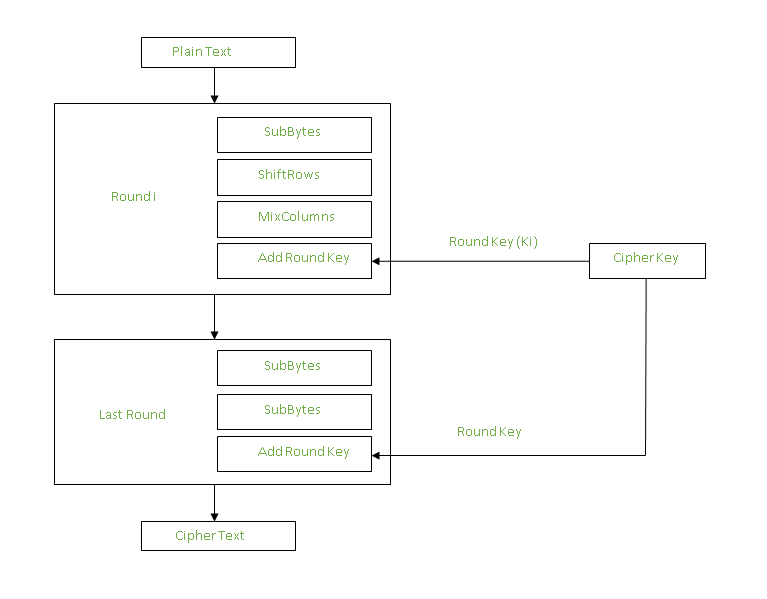
Figure: Structure of AES III. Implementation The AES algorithm is based... | Download Scientific Diagram
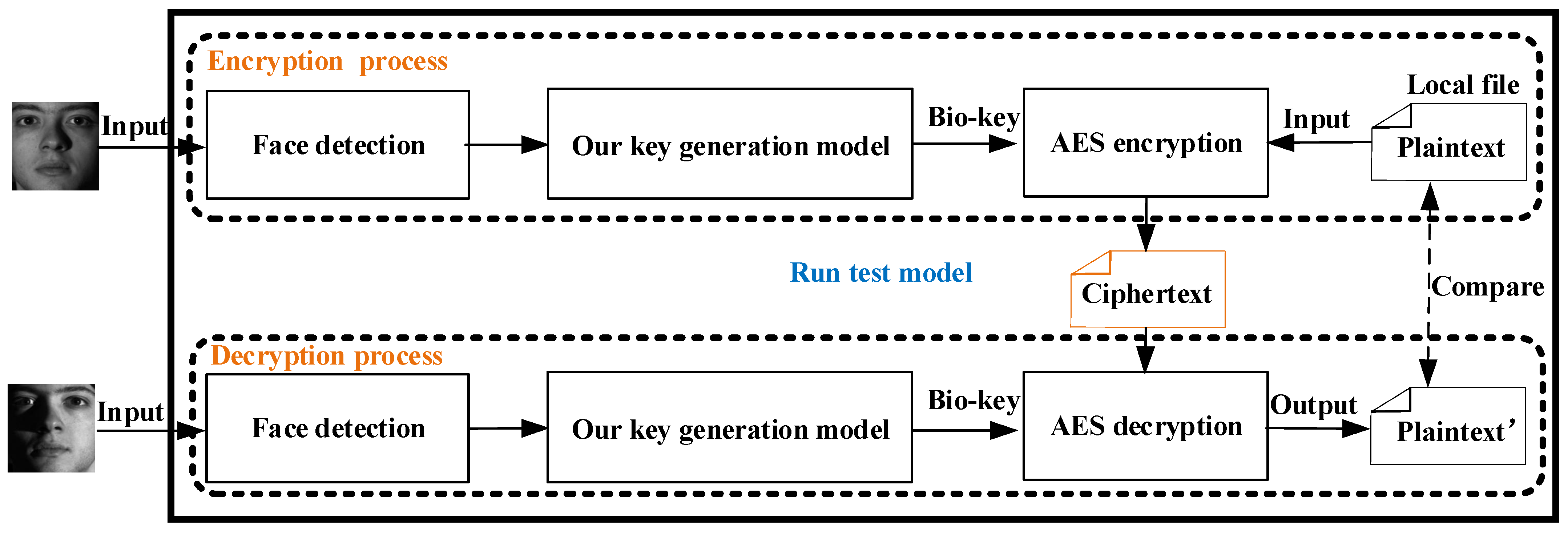
Applied Sciences | Free Full-Text | A Secure Biometric Key Generation Mechanism via Deep Learning and Its Application

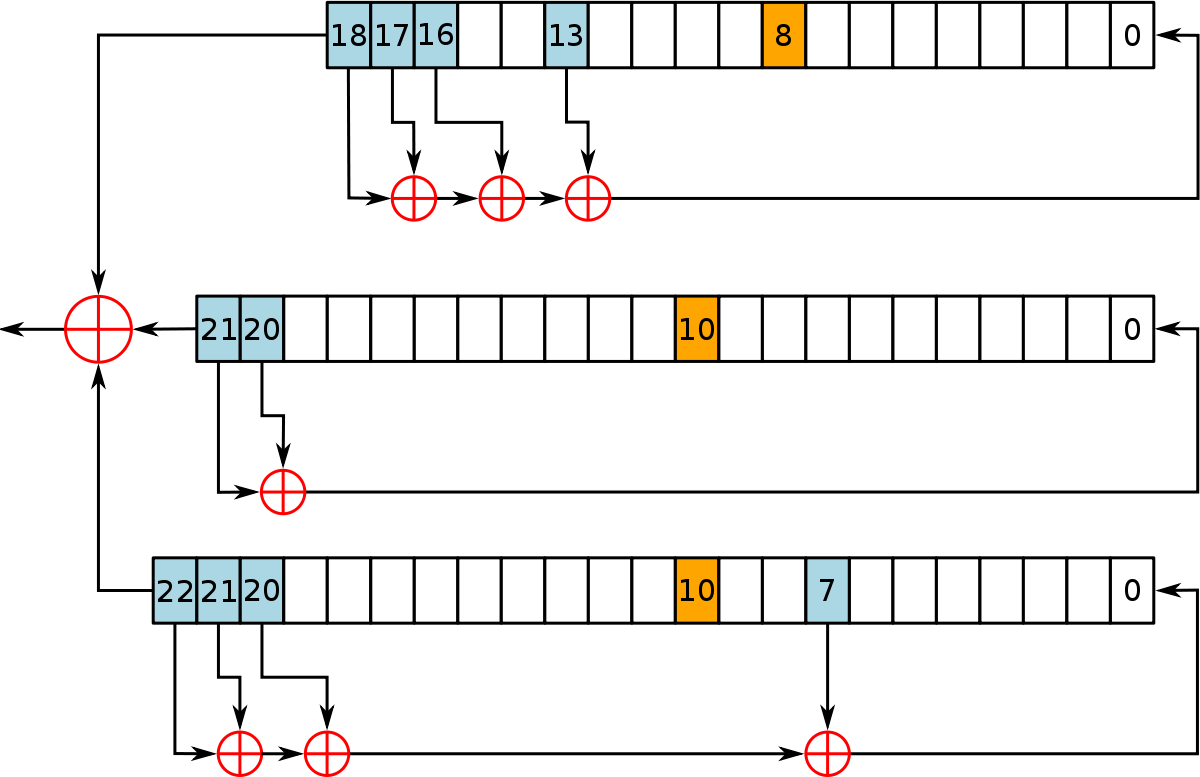
Applied Sciences | Free Full-Text | Omega Network Pseudorandom Key Generation Based on DNA Cryptography